Fishing. I’m sure you know what does it mean. Depending the place where you live, your age, family’s background, will, and circumstances so it’s quite possible you already fished alone or together friends, relatives or even with your grandpa!
Perhaps you weren’t interested in the fishing but more in the companion or just enjoying the nature around. In my childhood, I had several good moments fishing with my daddy, brother, relatives, and friends. Honestly, I ever liked to fish. Many times I got the fishes but quickly released them on the water again! Well, my daddy wasn’t happy with that but fishing for us was a hobby, not something we depend on to live as many families around the world does.
Now, living on a high cybernetic and cutting-edge techy world, there is a different type of fishing. Do you know which one?
Phishing Scam. No, I didn’t write wrong. Phishing Scam is a type of online identity theft. It uses email and fraudulent websites that are designed to steal your personal data or information such as credit card numbers, passwords, account data, or other information.
Do you want to know a little bit more about this type of ‘phishing’ and how to protect you and especially your parents, grandma, grandpa, and others friends using the Internet, in general, innocent victims of those scams?
Let’s listen a dialog between a grandson and his grandpa during a real fishing about how that grandpa recently was a victim of “Phishing scam” and the measures he took after with a little help of his grandson.
– Hey grandpa! I’m glad we’re here at the Lake Blue fishing on this beautiful and shining morning of summer! Thanks for inviting me.
– Do you remember the last time we’re here on this lake?
– Sure, grandpa. I was 7 years old only. There were so many fishes I even need to use my fishing lures! Just put the hook in the water and voilá!
– Indeed, my grandson! That time was a great fishing’s day! By the way, I never imagined that one day I would be caught as a fish!
– What do you mean, grandpa?
– My bank account was stolen via a such “Phishing Scam”! I think your grandma told you that, right?
– Yes, she told me! I was there explaining to her what is Cloud Computing and Big Data. So what happened?
– Every day I check my e-mails. So, on a Monday morning I did a read an email from the bank where I have an account. They said on the message, an unusual attempt to access my online account was detected so there was a link to confirm and change my password. I clicked on the link then a pop-up with my bank’s logo showed up asking to confirm the branch code, account, current password and the new password. I completed all the information requested and done.
– Wow, grandpa! What happened next???
– A couple of hours after, my bank’s account manager called to confirm some withdraws because the system detected a nonstandard behavior on my account. Happily, they called me then blocked the access to my account.
– That was terrible! Did you lose money?
– Yes, I did. But the situation could be worst if the bank didn’t detect the scam. My identity was under risk too! So, my grandson, what “Phishing Scam” exactly is?
– Well, let’s think on a real fishing as we’re doing now on this lake. We don’t know how many and neither all types of fishes are under the water, right?
– Correct, my grandson.
– We are sure about two things: there are many fishes and we want fish some! So, what do you do usually as a first step on a fishing?
– My grandson, there are some basic steps. Fishing is a art. Art of fishing.
– Grandpa, tell me the basics steps then I’ll correlate them with the “Phishing Scam”, an Art of Hacking accordingly the Cybercriminals!
– The first step is: Basic knowledge – know what kind of fish you want to catch, and learn about their habits and habitat. Time of day is important; some fish will bite best in the morning, while others are hungrier in the afternoon. Some like cold water and others stick to the warmer shallows. Be sure to check the weather report before you head out on the waterways.
– Interesting grandpa! Professional hackers or known also as Cybercriminals do the same! They also study computer and Internet users’ behavior. They know what attracts young people. Retired ones as you, grandpa. Which day of the week is best to send e-mails. If you visited some websites or social networks, then some ‘cookies’ or tracks still in your machine.
– So, I got a lot of e-mails every day. Is there something I should do at the very first moment?
– Oh, yes, grandpa. Many e-mails are sent to verify if the recipient really exists, if it’s a valid e-mail address. Before opening an e-mail, verify who is the sender? Do you know him/her or the source? If don’t, just delete the message, do not open it. If you open a unknown message, inside they have some links and images prepared to automatically send back to the sender a read receipt so they know you exist and it’s a valid e-mail.
– That’s interesting! Anything else?
– Sure. After checking the sender, check the subject. Is the subject something really relevant to you? Spelling and grammar mistakes? An idiom you don’t understand? Do not open it, just delete it.
– Right. So it’s possible only get a preview of a message before open up?
– Yes, it is. Most of e-mails clients like Outlook has the Preview mode or even the basic e-mail client at Windows 10 has this feature. You just see a few lines then you can select the messages and click on Delete.
– Understood, good tip!
– Now, what’s the second basic step for fishing? I mean, the real fishing!
– Second tip for a good fishing is: Bait. Even fish have different preferences when it comes to food. Use bait that your target fish enjoy. Cover the hook with the worm or other bait, so the fish gets set on a good hook when they chomp down on the tempting bait. Some artificial and electronic baits appeal to certain types of fish but not others. Don’t go looking for perch with bait designed to attract salmon. Shiny reflective lures can sun blind certain fish; use matted metal lures instead.
– Wow, grandpa! You’re the guy! So it’s a mistake thinking a bait serves for all kind of fishes, right?
– Totally, right! Some fishes are very careful. They don’t bite any bait. Also, they can realize something is wrong surrounding that bait. Others just observe the small fishes being caught then they runaway and rarely come back to the same place.
– It’s a quite interesting because the correlation with the Phishing Scam is the same. Cybercriminals also know which type of ‘bait’ attract immediately some people and others take more time. So they send thousands, millions of e-mails daily using the most different type of contents, subjects, and other tricks.
– Millions of e-mails daily? Is that true?
– Yes, grandpa. I worked some time ago on a customer where they got in average 10 million of SPAM messages every month! Inside of those messages there were poisoned links, malwares and others Phishing Scam stuff. So you can realize, they are not kidding! I’m talking about just one customer!
– It’s like a gigantic and global fishing! Sending millions of ‘poisoned’ baits in form of a message, if they got just 1% of victims that’s still in the millions level! Amazing terrifying!
– Correct, grandpa. Thus, when you got a Phishing Scam message, you’re not the only one! Although, if they got a lot of information about you then they can send more personalized poisoned e-mails. They still improving each day.
– Indeed, grandson, but in the cases where I already opened a Phishing Scam message, is there something I can do or verify to be sure it’s not a safe message?
– Of course, there is. Look this message on my smartphone. It’s a Phishing Scam message, see some details.
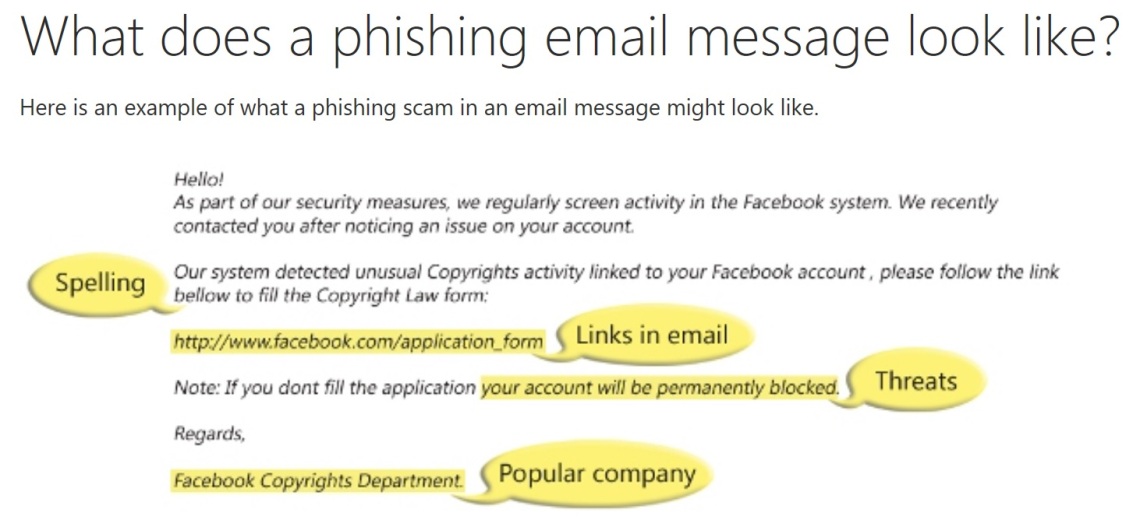
– Hmmmm, interesting, I can see some bad grammar and spelling errors.
– Perfect! You realized that now, right? Besides that, did you see there is a link in the body of the message? Beware of links in email. If you see a link in a suspicious email message, don’t click on it. Rest your mouse (but don’t click) on the link to see if the address matches the link that was typed in the message. On this case, look this:

– Can you see, grandpa, the address in light yellow does not match with the link showed? Links might also lead you to .exe files. These kinds of file are known to spread malicious software.
– Oh! Monkeys bite me, Batman!!! I ever realized that!
– Ha ha ha! That’s a really old expression, grandpa, it’s funny. Yes, this is a simple but very effective way to detect a Phishing Scam message. Do you see anything else suspect?
– Honestly, I don’t. Are there even more wrong things on this e-mail?
– Oh yes, there are. Look, this message is a Threat. Have you, grandpa, ever received a threat that your account would be closed if you didn’t respond to an email message? This email message I’m showing to you is an example of the same trick. Cybercriminals often use threats that your security has been compromised.
– Unbelievable! I got some messages like that! What else I should pay attention?
– Grandpa, as you can see here on this message, they do spoofing of popular websites or companies. Scam artists use graphics in email that appear to be connected to legitimate websites but actually take you to phony scam sites or legitimate-looking pop-up windows.
– Holy ingenuity, batman!
– Ha ha ha! Also, the cybercriminals use web addresses that resemble the names of well-known companies but are slightly altered. Instead, for example, using “Bank of America” the correct one, they can use “Bank of the America”. They just added a word: “The”.
– I see. We really need pay attention to the details, isn’t? I’m appreciating all these fantastic tips!
– My pleasure, grandpa! What’s the third basic step for a good fishing?
– Peace and patience – keep noise to a minimum, but bring along something to help you pass time; be patient. Keep a close watch for any fishing line movement; a quick hard tug is a chance to hook a fish if you are ready, grandson!
– Cybercriminals do the same thing when doing Phishing Scam. They have patience and persistency. They never gave up. If a type of message is being blocked so they will change. They keep a close watch if a recipient opened a message or replied it. Even when they got a successful “Phishing”, in general, they wait some time, patiently, until do an attack and steal information or money via online methods.
– Do you mean, they don’t attack in the same day, I mean, they don’t “cook” the “fishes” just after caught them? Why? After a good day of fishing, I took the fishes to home thinking on the dinner and lunch a day after!
– Both things happen, grandpa. Some victims of the cybercriminals are stolen or hacked in the same day after a successful “Phishing Scam” day. But, they also keep some “fishes” or users only trapped in the hook. Most of times, the ‘fishes’, I mean the users, us human beings, don’t know your computer, accounts, password are compromised. Cybercriminals can use them as a botnet, it means a network of compromised computers and users, thus doing other attacks and still “Phishing Scam” through those ‘caught fishes’.
– I see, grandson! It’s similar the real fishing. We caught small fishes to use them as baits for the big ones!
– You got it! Many times, they got partial information then they wait until find out more. Sometimes, cybercriminals continue a “Phishing Scam” using other methods, as for example, Phishing Phone Calls. They want to gain your trust.
– Phishing Phone Calls? Oh my goodness!
– They do phone calls saying: “Hello Mr. Fool, we are from the bank XYZ. There are some attempts of unauthorized access on your bank account. It’s necessary to confirm some information. Could you confirm you birth date, Social Security number?” A trustful source, as a bank, has already this information. In cases like that you can ask for a phone number to call back, call your bank’s account manager or ask back some questions. If it’s not true, they hang up the phone call.
– You’re right, good tips again, thank you. Any additional tip?
– Use your e-mail client, Outlook or other, Security and Junk settings. In general, the automatic settings are the best. Use the option, Block the Sender. Another option very common, Submit as SPAM. In Outlook, for example, there is an option, Trust Center with a lot of settings to protect you against “Phishing Scam” and others malwares. I can assist you on that, OK, grandpa?
– I appreciate your help, surely! I’m glad having this conversation. You know, dear grandson, computers and technologies are not something I really enjoy or spend my time on it. I prefer do other things but on these days it’s almost impossible live without using computers and smartphones.
– Grandpa, any other best practice for a good fishing?
– Two last ones: Silence is gold in the fishing so let’s concentrate now in the lake and once we have fished some, it’s time for our inner chef, Grandma, to take over!
– We have a deal, grandpa! Hey! I think a fish pulled the hook!
Author: Alexandre Marins Augusto
Blogs: August Alexander & TechNet – Microsoft Alexandre Marins (Tech & Security)
Sources: Microsoft Safe & Security Center, LiteFighter, Picture: Fishing with Grandpa by Jack Sorenson.
More articles:


